SQL Injection (SQLi) is a classic web security vulnerability, yet it remains one of the most dangerous and frequently exploited. It allows attackers to interfere with an application’s database queries, leading to unauthorized data access, manipulation, and even full system compromise.
In this comprehensive guide, we’ll dive deep into what SQLi is, how various types are exploited, and crucially, how to prevent these attacks to safeguard your applications and data.
Tables of Contents
What is SQL Injection (SQLi)?
SQL Injection is a security flaw that lets hackers sneak harmful commands into a website’s database through input fields. By doing this, they can:
- Steal private data—like passwords, credit card info, or personal details—that they shouldn’t be able to access
- Change or delete data in the database, which can mess up how the website works16.
- Take control of the system in serious cases, possibly letting them shut down the website or even break into other parts of a company’s network.
In short, SQL Injection can cause big problems, including stolen information, broken websites, and major security risks.
Detecting SQL Injection Vulnerabilities
SQL Injection vulnerabilities can be found by testing the website in a careful way, either by hand or using special tools.
Manual Testing:
- Single Quote Test: Put a single quote (‘) in input fields and see if the website shows errors or behaves strangely.
- Boolean Test: Try adding conditions like
OR 1=1(always true) orOR 1=2(always false) to see if the website responds differently. - Time Delay Test: Use commands that make the database wait (like
SLEEP()) and check if the website takes longer to respond. - Out-of-Band Test: Use special code that makes the website contact an outside server if the test works, which means there’s a vulnerability.
Automated Testing:
- Use Tools: Tools like Burp Scanner can quickly check for SQL Injection problems, making the process faster and easier.
Common SQL Injection Examples & Techniques
In this blog, we will explore the two most common examples of SQL injection: Retrieving Hidden Data and bypassing login security. These examples show how attackers can view sensitive information and trick authentication systems.
Retrieving Hidden Data
Below is a shopping application that shows products by filtering them with a category parameter. The SQL query used is:
SELECT * FROM products WHERE category = 'Gifts' AND released = 1
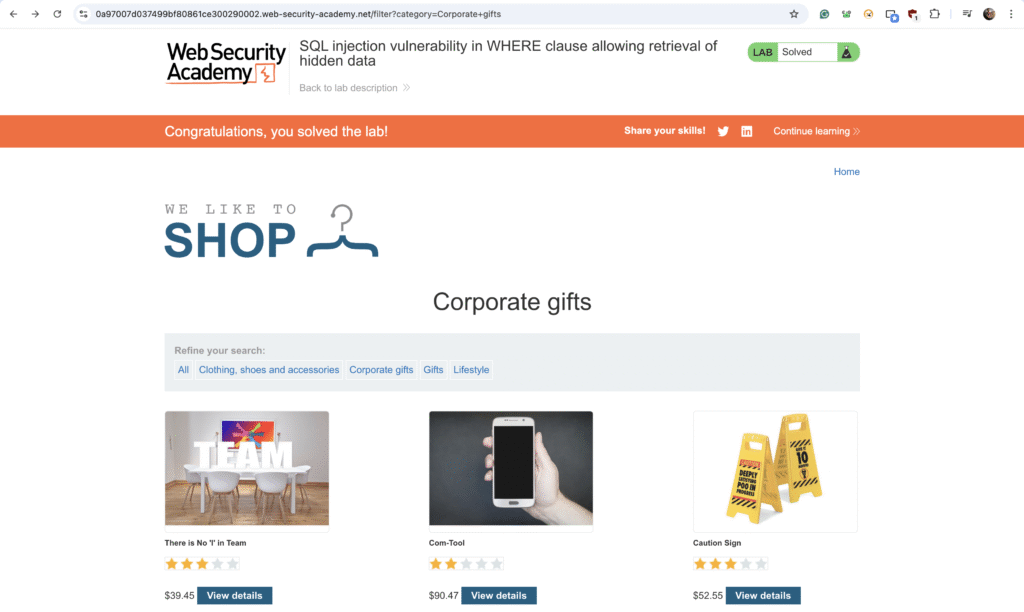
First, we’ll check if the category parameter is vulnerable to SQL injection by adding a single quote (‘) to the query.
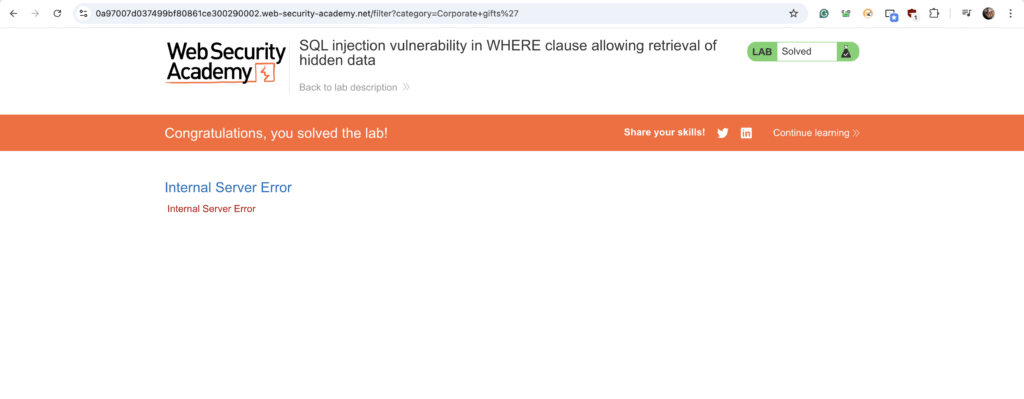
As shown in the screenshot above, we received an “Internal Server Error,” which indicates that our input affected the SQL query being processed on the backend.
An attacker could inject '-- (SQL comment) to bypass the AND released = 1 condition:
This results in the query: SELECT * FROM products WHERE category = 'Gifts'--' AND released = 1 which effectively removes the released restriction, displaying all products, including unreleased ones.
Similarly, using '+OR+1=1-- can display all products in any category:
Resulting in: SELECT * FROM products WHERE category = 'Gifts' OR 1=1--' AND released = 1.
Since 1=1 is always true, all items are returned.
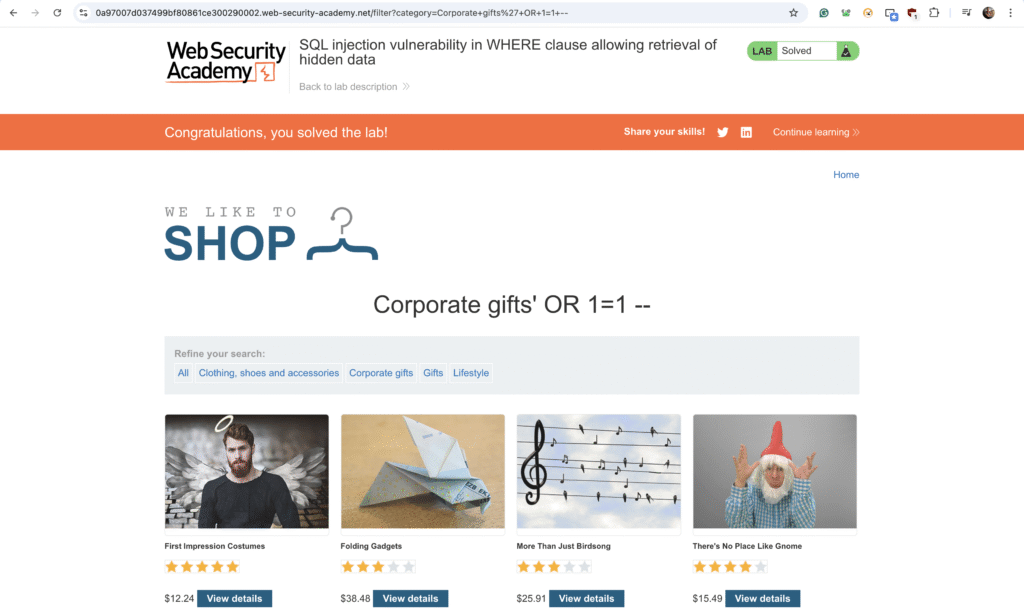
Now, when we inject ' OR 1=1 -- into the query, you can see that all the products available in the store are displayed
Login Bypass – Subverting Application Logic
The login form shown below uses the following SQL query to check user credentials:
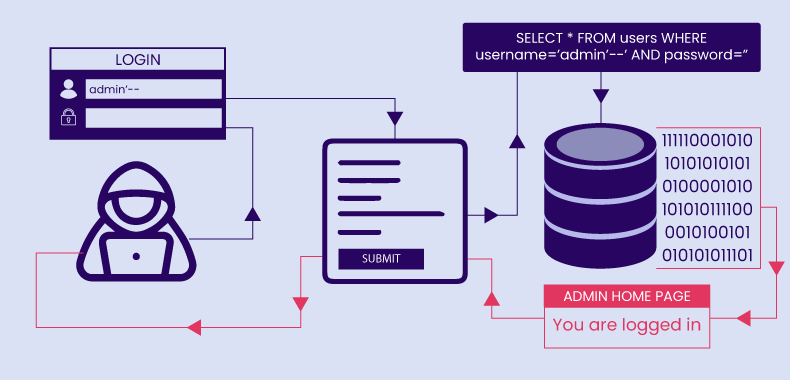
SELECT * FROM users WHERE username = 'wiener' AND password = 'bluecheese'
An attacker can bypass the password check by injecting '-- into the username field. For example, submitting
as the username and a blank password:
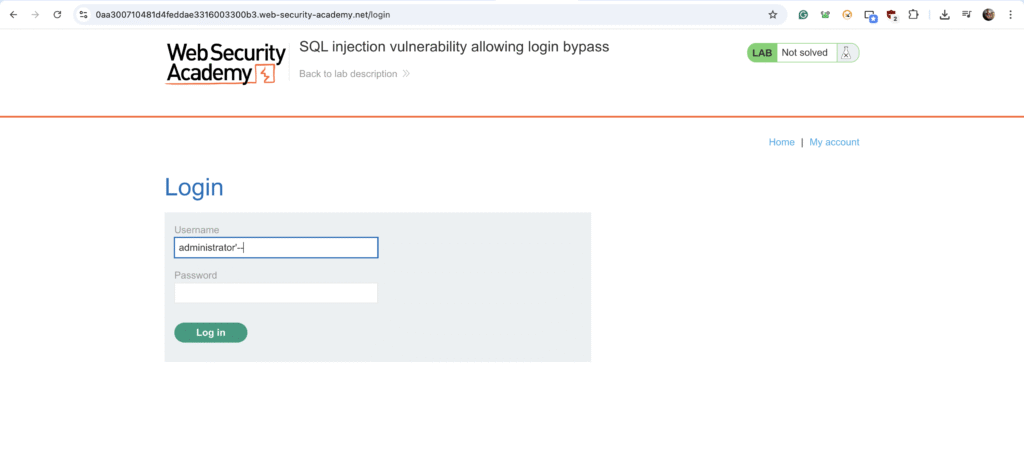
SELECT * FROM users WHERE username = 'administrator'--' AND password = ''
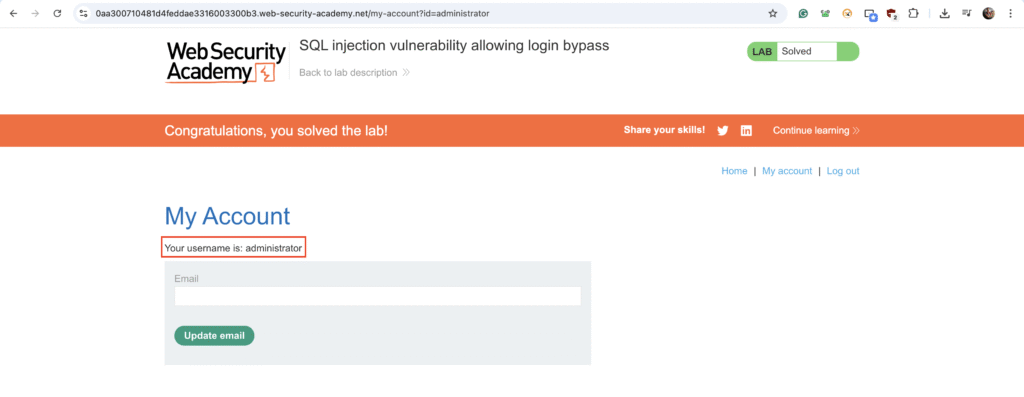
This query authenticates the attacker as ‘administrator’ without needing the correct password.
Conclusion
SQL injection remains one of the most dangerous vulnerabilities in web applications today. As demonstrated, simple attacks like injecting a single quote or using conditions such as ' OR 1=1 -- can allow attackers to bypass authentication and access sensitive data. These examples highlight how critical it is for developers to use secure coding practices and input validation. By understanding how SQL injection works, you can better defend your applications against these common threats and protect user information from unauthorized access. Always remember: security is a continuous process, and staying vigilant is key to safeguarding your system.