Network reconnaissance is a crucial first step in ethical hacking and cybersecurity. It helps identify the devices, services, and open ports in a network, laying the foundation for a deeper security analysis. One of the most popular tools for this purpose is Nmap (Network Mapper). Nmap is powerful yet beginner-friendly, making it an essential tool for aspiring ethical hackers and cybersecurity enthusiasts. In this blog, we’ll break down the basics of Nmap and guide you through its essential features in simple, easy-to-understand terms.
Table of contents
What is Nmap?
Nmap, short for Network Mapper, is an open-source tool used to discover hosts, services, and open ports in a network. It’s like a Swiss Army knife for network scanning. Whether you’re a beginner or a seasoned professional, Nmap can help you:
- Identify devices connected to a network.
- Discover open ports and the services running on them.
- Detect operating systems and software versions.
- Perform vulnerability scans.
Why Should You Learn Nmap?
Nmap is a cornerstone of network reconnaissance and is widely used in penetration testing, vulnerability assessments, and network troubleshooting. Here are a few reasons why you should learn it:
- Free and Open-Source: Nmap is completely free, and its codebase is accessible to anyone.
- User-Friendly: It offers both a command-line interface and a graphical interface (Zenmap) for ease of use.
- Widely Used: It’s a standard tool in the cybersecurity field, making it a valuable skill for ethical hackers.
Getting Started with Nmap
Before diving into commands, you need to install Nmap. It’s available for all major operating systems, including Windows, macOS, and Linux. Visit nmap.org to download the version for your OS.
Once installed, open your terminal or command prompt to start using Nmap.
Basic Nmap Commands
Let’s explore some basic Nmap commands to help you get started.
1. Scanning a Single Host
To scan a specific IP address or hostname:
nmap <target>Example:
nmap hackerhaven.io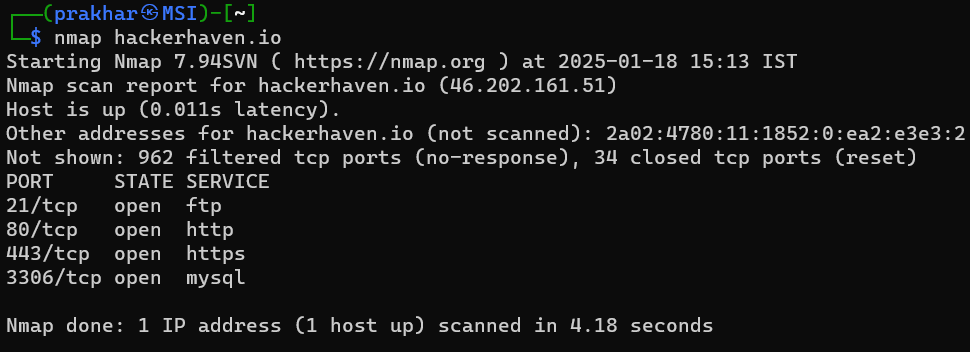
This command provides basic information about the target, such as open ports and services.
2. Scanning Multiple Hosts
You can scan multiple targets by separating them with spaces or using a range:
nmap 192.168.1.1 192.168.1.2
nmap 192.168.1.1-10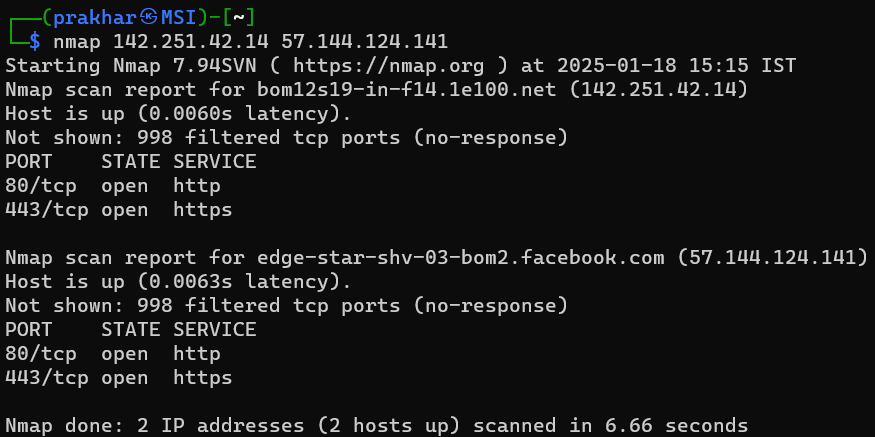
3. Scanning an Entire Subnet
To scan an entire subnet, use CIDR notation:
nmap 192.168.1.0/24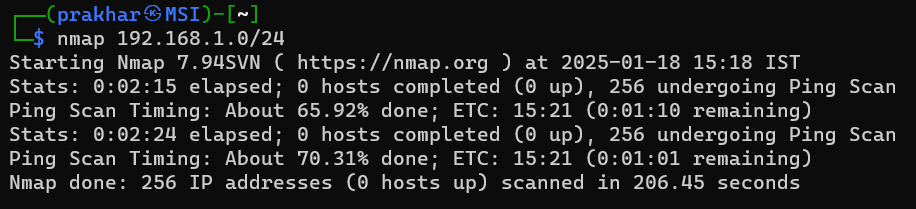
This will scan all 256 IP addresses in the subnet.
4. Detecting Operating Systems
Nmap can guess the operating system running on a host:
nmap -O <target>Example:
nmap -O hackerhaven.io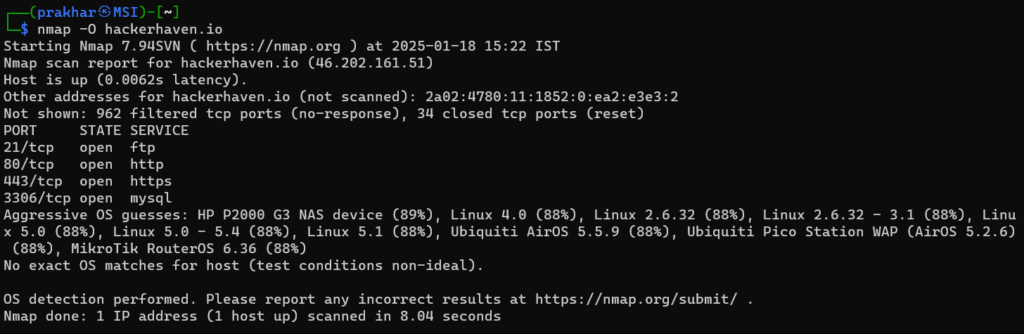
5. Scanning for Specific Ports
By default, Nmap scans the top 1,000 commonly used ports. To scan specific ports:
nmap -p <port> <target>Example:
nmap -p 80,23 hackerhaven.io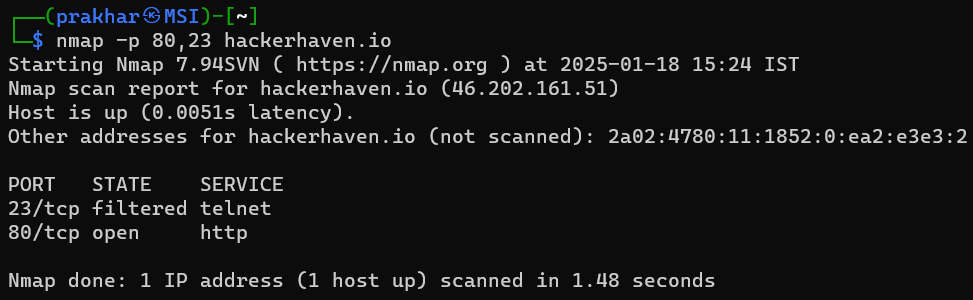
6. Aggressive Scanning
For detailed information about a target, use the aggressive scan option:
nmap -A <target>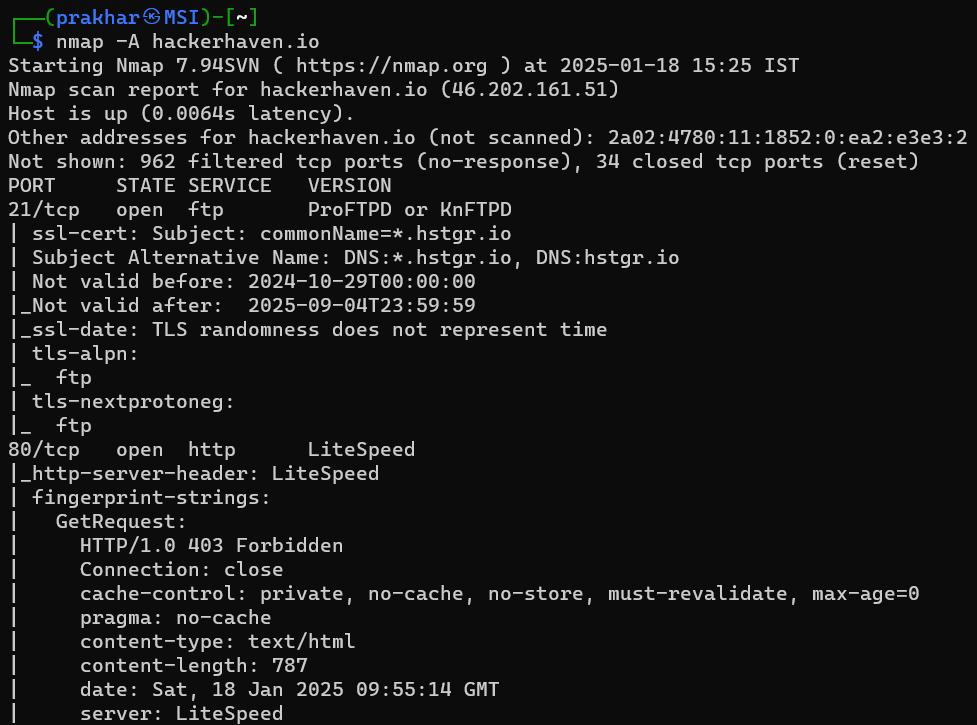
This provides details about the operating system, services, and more.
7. Saving Scan Results
To save the scan results for future reference:
nmap -oN output.txt <target>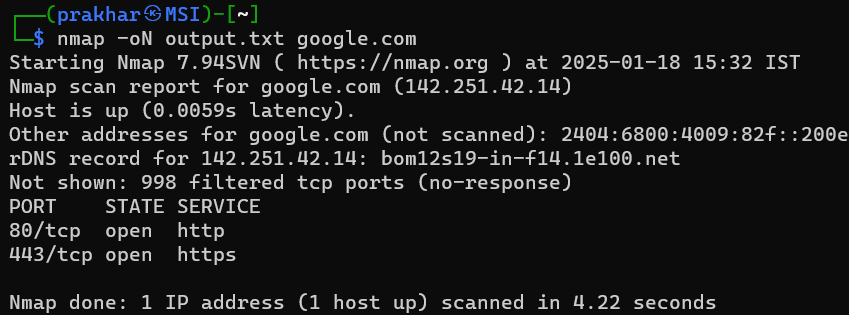
The results will be saved to a file named output.txt.
Tips for Using Nmap Effectively
- Start Small: Begin with basic scans and gradually explore advanced options as you become more comfortable.
- Understand the Results: Take time to learn what each part of the scan output means.
- Practice Safely: Only scan networks you own or have explicit permission to test.
- Experiment with Options: Use Nmap’s extensive documentation to learn about its various features and advanced capabilities.
Why Ethical Hackers Rely on Nmap
For ethical hackers, Nmap is a go-to tool for gathering intelligence during penetration testing. It helps identify potential vulnerabilities and provides a roadmap for deeper investigations. Ethical hackers use Nmap responsibly to improve security by identifying and addressing weaknesses before malicious actors can exploit them.
Conclusion
Nmap is an indispensable tool for anyone looking to understand and secure networks. With its simple commands and powerful capabilities, it’s the perfect starting point for beginners in cybersecurity. By mastering Nmap, you’ll gain valuable skills that will serve you well in ethical hacking, penetration testing, and network administration. Start exploring Nmap today and take your first step into the exciting world of network reconnaissance. Remember, with great power comes great responsibility—always use Nmap ethically and with permission.