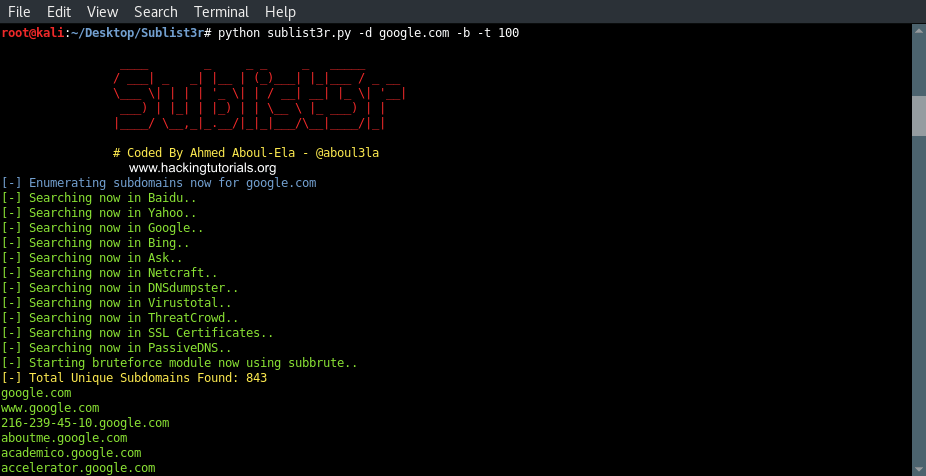
Subdomain enumeration is a crucial step in reconnaissance, especially for ethical hackers and cybersecurity professionals. It helps uncover hidden subdomains of a target domain, offering insights into potential vulnerabilities and security gaps. Among the many tools available, Sublist3r stands out for its simplicity and efficiency. In this guide, we’ll walk you through the basics of Sublist3r and how to use it effectively for subdomain discovery.
Table of contents
What is Sublist3r?
Sublist3r is an open-source Python-based tool designed for subdomain enumeration. It automates the process of identifying subdomains by querying various search engines and APIs, including:
- Bing
- Yahoo
- Baidu
- Ask
- VirusTotal
- ThreatCrowd
- Netcraft
- DNSdumpster
- ReverseDNS
With Sublist3r, ethical hackers and penetration testers can quickly gather valuable information during the reconnaissance phase of a security assessment.
Installing Sublist3r
There are multiple ways to install sublist3r the two most common methods are mentioned below
1. apt
If you are using Kali Linux or any Debian-based OS then you can use this command
sudo apt install sublist3r2. Git
If you want to install sublist3r using git use the following commands
git clone https://github.com/aboul3la/Sublist3r.git
cd Sublist3r
pip install -r requirements.txtSublist3r is now ready to use!
How to Use Sublist3r
Using Sublist3r is straightforward. Follow these steps:
Basic Command
To enumerate subdomains for a target domain, run:
sublist3r.py -d example.comHere:
sublist3r.pyinvokes the tool.-d example.comspecifies the target domain.
Advanced Options
Sublist3r offers additional flags to customize your scan:
Save Results to a File
Save the discovered subdomains to a text file for later use
sublist3r.py -d example.com -o results.txtUse Specific Search Engines
Restrict your search to certain engines using the -e flag
sublist3r.py -d example.com -e google,bingEnable Verbose Mode
View detailed output during the scan
sublist3r.py -d example.com -vPractical Tips for Using Sublist3r
- Combine with Other Tools: Use Sublist3r alongside tools like Nmap or Burp Suite for deeper analysis.
- Verify Results: Double-check discovered subdomains using DNS resolution tools to confirm they are active.
- Respect Legal Boundaries: Always get permission before scanning a domain to avoid legal issues.
- Update Regularly: Sublist3r’s database and functionality improve over time, so keep it updated.
Conclusion
Sublist3r is an essential tool for anyone involved in ethical hacking or cybersecurity. Its simplicity, speed, and effectiveness make it a go-to solution for subdomain enumeration. By integrating Sublist3r into your workflow, you can uncover hidden parts of a target’s online infrastructure and strengthen your reconnaissance efforts.
Start exploring Sublist3r today and take your ethical hacking skills to the next level. Remember, always use this tool responsibly and within the bounds of the law. Happy hacking!