Table of content
Introduction
In the digital age, our online identities are scattered across various social media platforms, each tied to a username. Whether you’re conducting cybersecurity research, performing digital footprint analysis, or simply curious, finding all accounts associated with a specific username can be a daunting task. Enter Sherlock, a powerful open-source tool designed to Hunt social media account.
Sherlock simplifies the search for social media accounts by scouring hundreds of platforms to uncover accounts linked to the desired username. In this blog, we’ll explore how Sherlock works, its practical applications, and how you can use it effectively for ethical purposes. Stay tuned to learn how this tool empowers cybersecurity enthusiasts and researchers to easily track down usernames across the web.
You can find this tool by clicking here
Installation
There are many ways you can use to install this tool
1. pip
pipx install sherlock-projectNote:- pip may be used in place of pipx
2. docker
docker run -it --rm sherlock/sherlock3. dnf
dnf install sherlock-projectBasic Usage
1. Opening help menu
To open the help menu type in
sherlock -h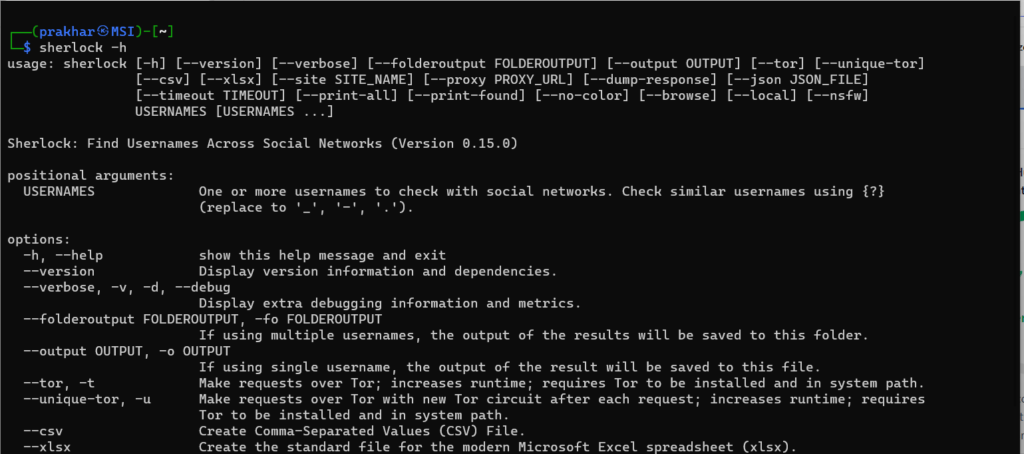
2. Searching one user
If you want to search for only one user you can type in
shelock [user_name]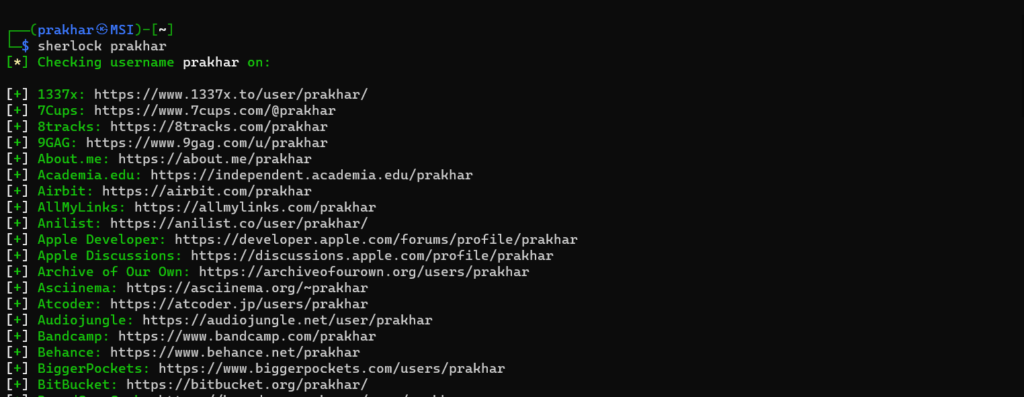
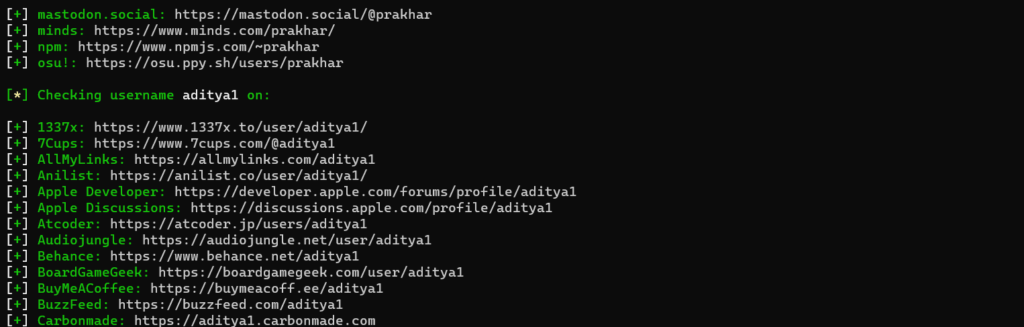
3. Searching multiple users
If you wish to search for multiple users you can type in
shelock [username-1] [username-2]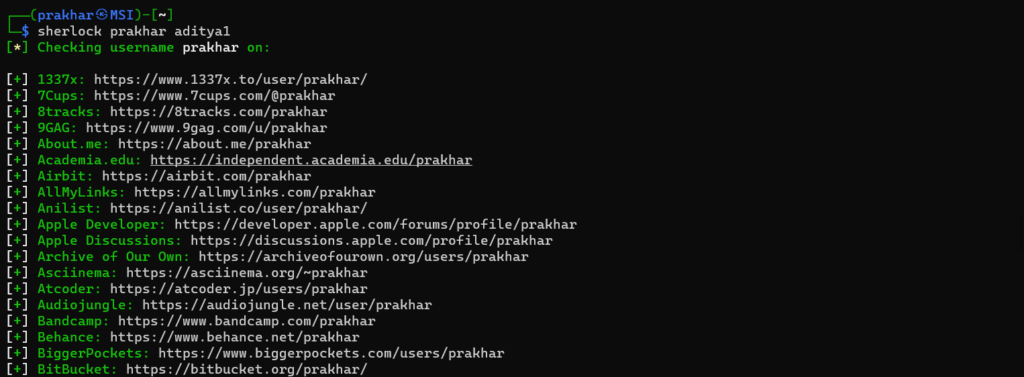
Advance usage
1. Saving the result
If we want to save the results of the search we can use -o option
sherlock [user_name] -o output.txt
2. Enabling the verbose/debugging mode
If we want to see behind the scenes how this tool works we can use the -v option
sherlock [user_name] -v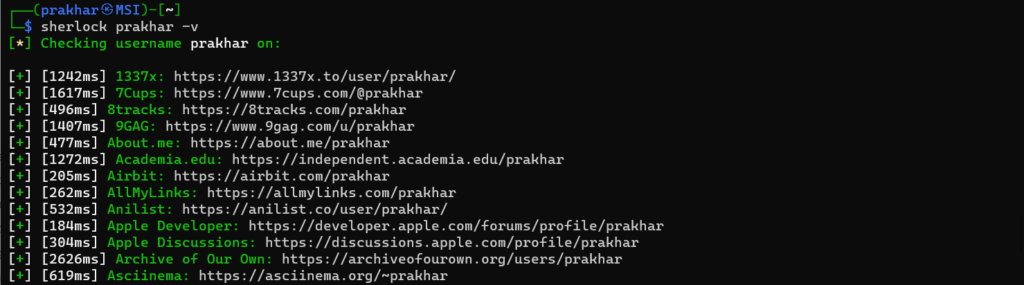
3. Printing sites where the username was not found
To know the site where the username was not found we can use –print-all option
sherlock [user_name] --print-all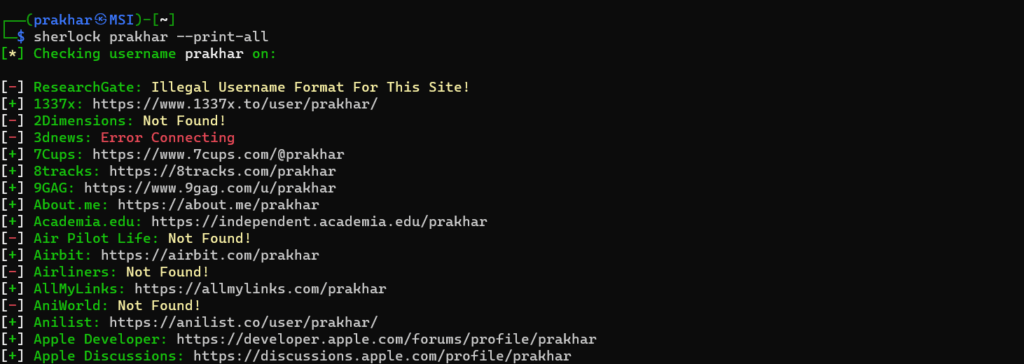
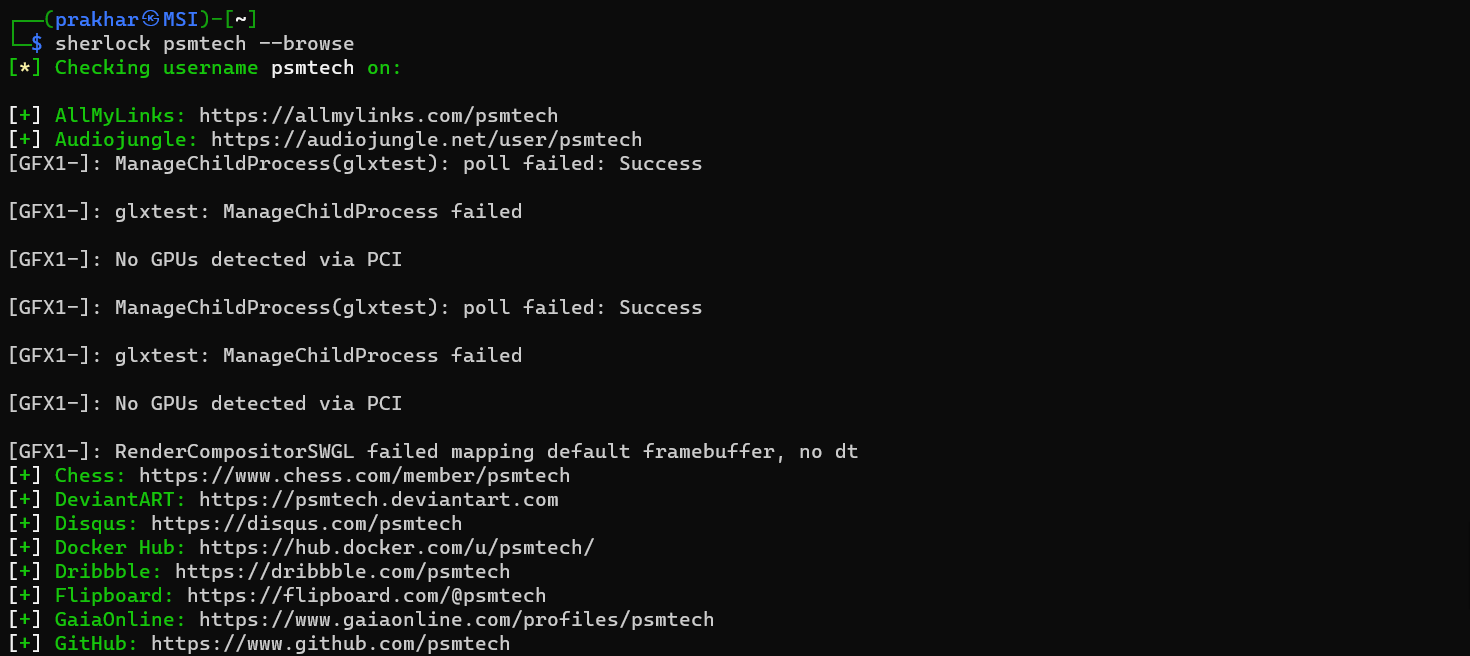
4. Opening the result on the browser
If you want to open the result on the browser automatically you can use the -b option
sherlock [user_name] -b